Federated Authorization
In a comment to a previous blog entry here, James McGovern asks
Does Federated Identity sometimes require Federated Authorization? If so, how come this isn’t ever discussed. Maybe you could address in future blog entry…
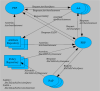
There are two models here. In the first model, a given user has a profile (set of attributes) stored at an attribute provider (which may or may not be the same as that user’s identity provider). The user goes to a service provider, the service provider receives a SAML 2.0 Assertion containing some set of attributes, and the service provider acts as both the policy decision point (PDP), deciding, on the basis of the user’s identity (including the attributes), which resources the user may access, and the policy enforcement point (PEP), restricting the user’s access appropriately. Here’s a real example in the enterprise space…
Sun has deployed federated single sign-on with BIPAC - BIPAC is the Business Industry Political Action Committee provides expert policy analysis, research and communications on campaigns and elections, and fosters business participation in the political process. Sun employees can access political information on the BIPAC website - who their elected representatives are, their voting record etc.
When I go to the BIPAC site, it redirects me to Sun, I log in with my Sun employee number and password and I’m redirected back to BIPAC with a SAML assertion containing a number of attributes - iirc, whether I’m a US citizen, whether I’m a member of a ‘restricted class’ of employees and my zip code. Note that the assertion does not identify me personally - it only tells BIPAC that I am a Sun employee with these attributes. Now the BIPAC site can act as the PDP, deciding what I can access, based on those attributes, and as the PEP, constraining my access to the BIPAC site according to those decisions.
In the second model (which is what I think James means by ‘federated authorization’), the service provider is still a policy enforcement point, but the policy decision point is elsewhere. In our BIPAC example, the BIPAC site would still redirect me to Sun for authentication, but need not receive any attributes in the SAML assertion - just a pseudonym (SAML Name Identifier) that it can use to refer to me; again, BIPAC doesn’t know who I am - the pseudonym can be a one-time identifier - used in this interaction, but never re-used - so I can’t be tracked across visits. Now the BIPAC site can make an authorization request of a PDP at Sun, including my pseudonym and a reference to the resource I want to access. The PDP evaluates policy, essentially doing the same thing as the BIPAC PDP did in the previous example, and returns a response to BIPAC that indicates whether access to the resource should be allowed or denied.
Having these two models allows us to factor out authorization and put it where it makes sense. It may well be that it is the service provider that is responsible for policy, based on information provided by an attribute provider (model 1), or, alternatively, the service provider may simply request an authorization decision from a PDP, without being party to the data underlying the decision (model 2).
In terms of specs, both SAML and WS-Federation enable model 1 - passing attributes in assertions which are themselves carried in authentication responses. XACML is the basis for model 2, and is profiled for use with SAML by the SAML 2.0 profile of XACML v2.0 [PDF]. I’m not aware of any commercial products that implement this specification today (perhaps that’s why no vendors are talking about it?), but OpenSSO is a good place to go to talk about requirements and implementation - you can sign up to the ‘users’ mailing list here.
Does this answer your question, James?
UPDATE - perspectives on this from
And responses from James -
Comments
Paul Madsen
Pat, I swear I did not read your post before writing mine. Cross my heart swear on double malt (or whatever the good stuff is) paul
Thought Leadership
[Trackback] Federated Identity sometimes requires Federated Authorization. A continuing discussion on what industry thought leaders aren’t talking about…
Pat
Ah, now, Paul. "If single malt is good, then double malt must be better". Single malt means that it came from a single distillery. A double malt would be a blend of malts (technically, a vatted malt) from two distilleries. Allowing the blender some latitude produces a different result from sticking to one distillery, but better? Well - I guess I'll need to do some intensive research :-)
One double malt I can heartily recommend is The Peat Monster, which combines Caol Ila with Ardmore. Hmm - maybe it's time for another whisky posting...
trashcan.org
[Trackback] Early last month, James McGovern (the Hartford) and Pat Paterson (Sun) exchanged some thoughts here and here on the concept of Federated Authorization. James does a good job outlying a use case and Pat does similar in describing what the protocols mig…
Leave a Comment
Your email address will not be published. Required fields are marked *